-
No tricks, just treats – it’s the end of Windows Server 2012
Here at Datcom HQ, we’ve been marking the end of Windows Server 2012 with a rather delicious slice of spooky cake. Here’s everything you need to know about what’s happening with the server and what to do next. If you’re still running Windows Server 2012 operating system, you could be in for a spine-chilling surprise,…
-
The Datcom brand gets a refresh
We believe that every business deserves the best possible service when it comes to IT. Our commitment to excellence and to staying ahead of the curve is in our DNA.
-
Why Managed IT Services are good for your business
Managed IT Services is a broad term that’s used a lot in the IT industry. So what exactly is it?
-
What are the security risks of cloud computing?
There are lots of benefits to cloud computing, but there are some security factors to think about. Here’s our quick guide.
-
What is Cloud Computing?
The term ‘cloud computing’ has been around for a long time now, but if you’re not sure what it means, or why you need it, you’re not alone.
-
How to keep your IT equipment cool in the heat wave
With UK temperatures reaching record breaking temperatures this week, it’s crucial that you keep your IT infrastructure cool, so that your business can operate as normal.
-
Facebook scams, don’t be fooled
With around 2.9 billion monthly users, Facebook is one of the most popular social media sites. So it’s no surprise that this large audience is a target for scams and fraudulent activity. There are some common tricks that cyber criminals like to use. Take a look and see if you have come across any.
-
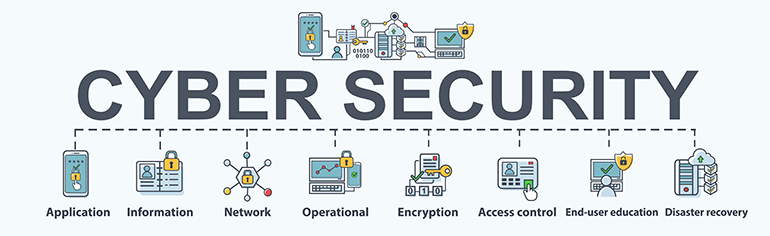
Show you’re serious about security with Cyber Essentials
Cyber Essentials (CE) and Cyber Essentials Plus (CE+) are accreditations that demonstrate your organisation’s commitment to safe digital practices. Here’s why we think they’re important and how you can get started.
-
Log4Shell Vulnerability
A vulnerability has been discovered in a piece of software called “Log4j”. This software, developed by Apache, is in millions of other applications to process logging information. Some high-profile use cases are the video game Minecraft, Apple iCloud, Amazon, Twitter, Tesla, the list goes on.
-
Ransomware and what you can do about it
You’ve probably heard of it, and you know it’s not good news. Here’s what you need to know about ransomware and what you can do about it.